Monitoring the continuous operation of the Microsoft 365 services is a critical part of the administration process, and the Microsoft 365 admin center includes a Health menu that provides a real-time display of the status of the individual services when administrators select the Service Health option, as shown in Figure 4-17.
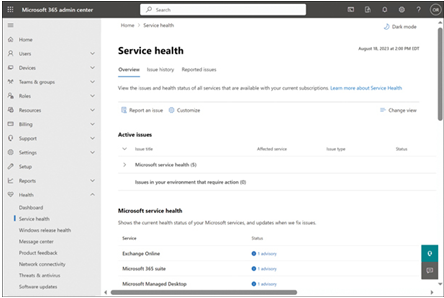
FIGURE 4-17 The Service Health page in the Microsoft 365 admin center
In addition to displaying the healthy services, the Service Health screen also lists other service status conditions:
- Advisories Indicates that the service is still available but that a known condition is inhibiting its performance. The condition might cause intermittent interruptions, affect only some users, or be limited in scope. In some cases, a workaround might be available.
- Incidents Indicates that a critical issue has been discovered that is rendering all or a significant part of the service unavailable or unusable. Typically, incidents are updated on their detail pages with information about the issue’s investigation, mitigation, and resolution.
Selecting the Issue History tab on the Service Health page displays details about the resolved incidents and advisories, as shown in Figure 4-18, including the service affected, its current status, and the time the advisory was posted.
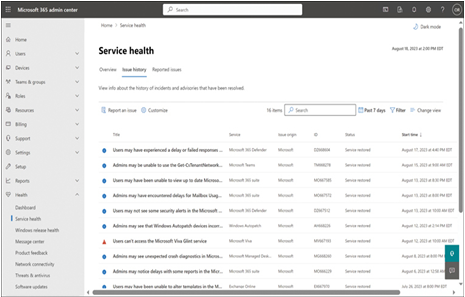
FIGURE 4-18 The Issue History tab of the Service Health page in the Microsoft 365 admin center
The Status indicators on the Service Health pages can have values such as the following:
- Investigating Indicates that Microsoft is aware of the issue and is currently gathering information before taking action
- Service Degradation Indicates that the service is experiencing intermittent interruptions, performance slowdowns, or failure of specific features
- Service Interruption Indicates that a significant, repeatable issue is occurring, which is preventing users from accessing the service
- Restoring Service Indicates that the cause of the issue has been determined and remediation is underway, which will result in service restoration
- Extended Recovery Indicates that remediation of the issue is in progress, but restoring service for all users may take some time or that an interim fix is in place that restores service until a permanent solution is applied
- Investigation Suspended Indicates that Microsoft is awaiting information from subscribers or other parties before the issue can be diagnosed or further action can be taken
- Service Restored Indicates that Microsoft has taken corrective action to address the issue and has successfully brought the service back to a healthy state
- Post-Incident Report Published Indicates that documentation on the issue has been published containing an explanation of the root cause and steps to prevent a reoccurrence
Each advisory or incident includes a detail page containing more information, as shown in Figure 4-19. This information may include a greater elaboration on the user impact of the advisory or incident and a log of its status as it proceeds through the process of being addressed, documented, and resolved.
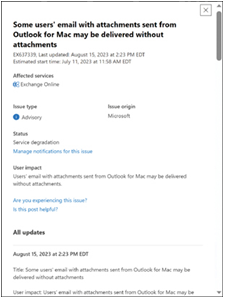
FIGURE 4-19 An advisory detail pane in the Microsoft 365 admin center
When an incident prevents administrators from signing in to the Microsoft 365 admin center console, a separate Microsoft 365 Service Health Status page (available at status.office365.com) indicates the health of the Microsoft 365 services, as shown in Figure 4-20.
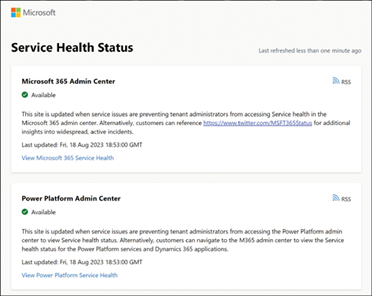
FIGURE 4-20 The Microsoft 365 Service Health Status page
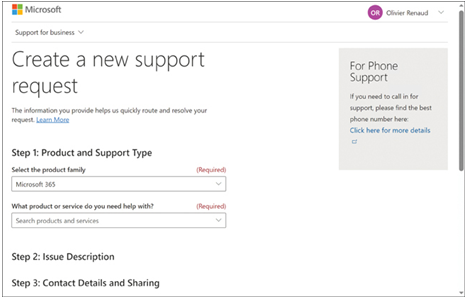
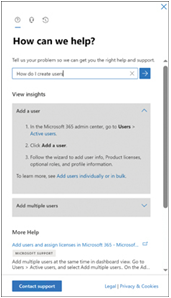
It is also possible to monitor the health of the various Microsoft 365 services in the Microsoft Entra admin center and create new service requests, as shown in Figure 4-21.
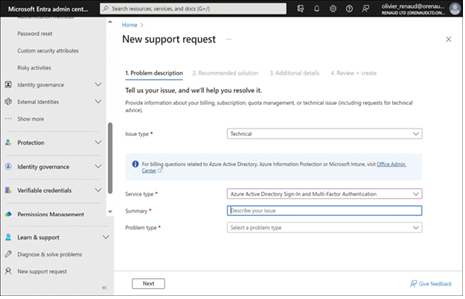
FIGURE 4-21 The New Support Request page in the Microsoft Entra admin center