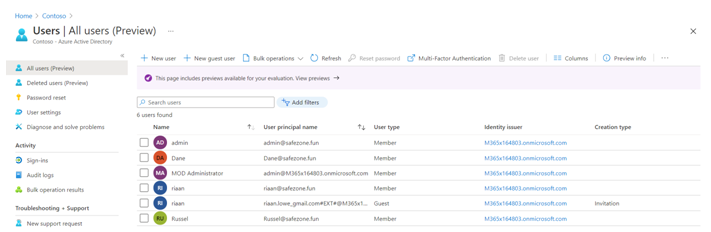
Part of an Azure administrator’s task is to understand what can be done from a user and group perspective within Azure AD. Let’s take a look at what we can configure for an Azure AD user account:
- Profile: This is where you can view and update information such as the name, user type, job information, and more.
- Assigned roles: This setting is where you can view all of the role assignments for that specific account; assignments can be in the form of eligible, active, or expired assignments.
- Administrative units: This setting displays the AUs that the user is part of.
- Groups: This setting displays the AD groups that the user is part of.
- Applications: This setting displays the application assignments.
- Licenses: This setting displays what licenses are currently assigned to the user account.
- Devices: This setting shows what devices are associated with the user account, including the join type such as Azure AD joined.
- Azure role assignments: This setting displays the resources on a subscription level to which the account has access.
- Authentication methods: This setting displays the authentication contact information, such as the phone number and email address for MFA. From here, you can also set the account to reregister for MFA or revoke current MFA sessions.
Now that we have reviewed all the user properties, let’s take a look at the group settings.
Azure AD groups have the following settings available:
- Overview: This displays the membership type, the source directory, the object ID, the creation date, and more.
- Properties: This setting displays the general settings for the group, such as the group name, the description, the group type, and the membership type, which can be changed here.
- Members: This setting displays all of the current members of the group; bulk operations can also be performed from here.
- Owners: This setting displays the owners of the group who can modify the group and the members within it.
- Administrative units: This setting displays the AUs that the group is part of.
- Group memberships: This setting displays all of the security groups that the group belongs to (nested grouping).
- Applications: This setting displays the application assignments.
- Licenses: This setting displays the licenses that are assigned to the group, which group members will inherit automatically.
- Azure role assignments: This setting displays the resources of a subscription level to which the group members have access.
- Dynamic membership rules: This setting displays the configuration rules; for dynamic groups, this is where you can change the configuration rules, which will affect the members of the group.
And that brings an end to the user and group properties. In this section, we have looked at all of the different settings for Azure AD users and Azure AD groups.
We encourage students to read up further by using the following links, which will provide additional information around managing group settings via the command line and also dive into external user attribute flows:
- https://docs.microsoft.com/en-us/azure/active-directory/enterprise-users/groups-settings-v2-cmdlets
- https://docs.microsoft.com/en-us/azure/active-directory/external-identities/user-flow-add-custom-attributes
Next, we are going to look at how to manage device settings within Azure.