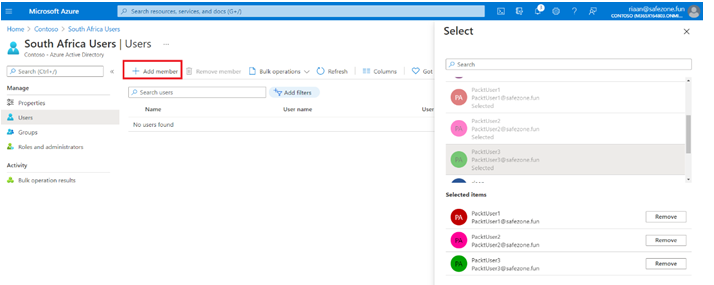
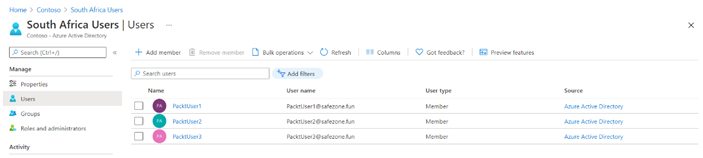
Performing bulk user updates is similar to managing single users (such as internal and guest users). The only property that can’t be set for multiple users is resetting the password. This has to be done for a single user.
Azure has also improved its bulk user settings by adding a drop-down menu that enables you to do the following via the downloadable CSV template and then re-uploading it:
- Bulk user creation
- Bulk user invitation
- Bulk user deletion
- Bulk user downloads
To perform a bulk user update, you have to perform the following steps:
- Navigate to the Users overview blade again in Azure AD.
- Select the Bulk operations drop-down menu:
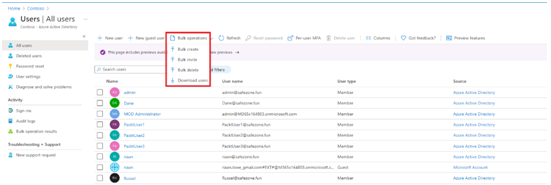
Figure 1.19 – The Azure AD bulk user operations option
- From the menu, select the action you want to complete; for example, select Download users:
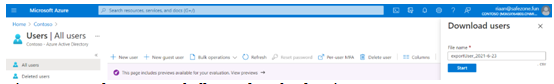
Figure 1.20 – The Azure AD bulk user download setting
- Also, you can update multiple users by selecting them and choosing to delete them or configure MFA for each user:
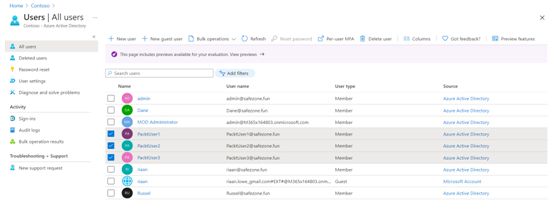
Figure 1.21 – The alternative Azure AD method for bulk user operations
This concludes our demonstration on how to perform bulk user updates and how it works.
We encourage students to read up further by using the following links, which will look at adding bulk users:
- https://docs.microsoft.com/en-us/azure/active-directory/enterprise-users/users-bulk-add
- https://docs.microsoft.com/en-us/azure/active-directory/enterprise-users/groups-bulk-import-members
In the next section, we are going to cover how you can manage guest accounts.
Managing guest accounts
You can also add guest accounts in Azure AD using Azure AD B2B. Azure AD B2B is a feature on top of Azure AD that allows organizations to work safely with external users. To be added to Azure B2B, external users don’t require a Microsoft work or personal account that has been added to an existing Azure AD tenant.
All sorts of accounts can be added to Azure B2B. You don’t have to configure anything in the Azure portal to use B2B; this feature is enabled by default for all Azure AD tenants. Let’s see how to manage the guest accounts by performing the following steps:
- Adding guest accounts to your Azure AD tenant is similar to adding internal users to your tenant. When you navigate to the Users overview blade, you can choose + New guest user from the top-level menu, as follows:
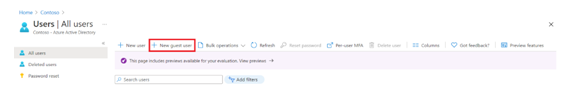
Figure 1.22 – The Azure AD Users blade to add a new guest user
- Then, you can provide an email address and a personal message, which is sent to the user’s inbox. This personal message includes a link to log in to your tenant:
- Select Invite user to add the user to your Azure AD tenant, and send an invitation to the user’s inbox:
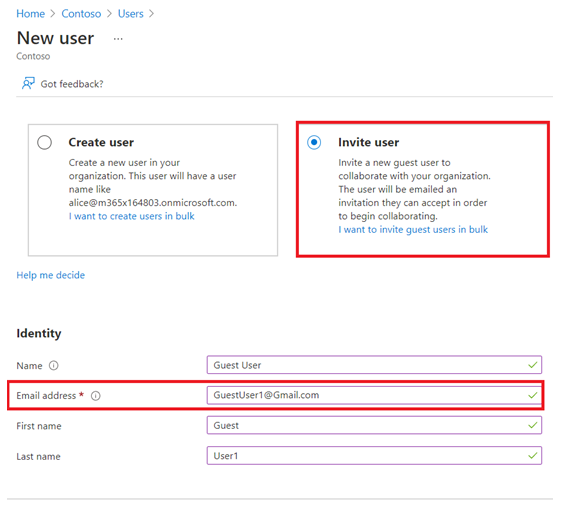
Figure 1.23 – Azure AD – inviting a guest user
- To manage external users after creation, you can select them from the Users overview blade. They will have a User type value, which is named Guest. Simply select the user from the list, and you will be able to manage the settings that are displayed in the top-level menu for this user, as follows:
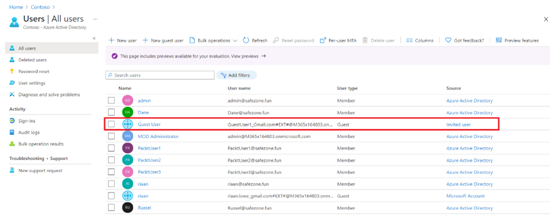
Figure 1.24 – The Azure AD Users blade displaying the account as Guest under User type
And that brings an end to this section. In this short section, we have reviewed guest accounts in Azure AD and learned how to configure them.
We encourage students to read up further by using the following links, which will provide additional information around restricting guest permissions:
In the next section, we are going to look at what Azure AD join is and how to configure it for Windows 10 devices.