As the proliferation and value of data increases over time, businesses, agencies, and individuals are becoming increasingly concerned with the privacy and protection of their data. Hundreds of regulatory bodies—private and governmental—quantify the nature of this data protection and publish standards for data storage and handling.
Some of the most common data privacy standards in use today are as follows:
- Federal Information Security Modernization Act (FISMA) Specifies how U.S. federal agencies must protect information
- Health Insurance Portability and Accountability Act (HIPAA) Regulates the privacy of personal health information
- Family Educational Rights and Privacy Act (FERPA) Regulates the disclosure of student education records
- Personal Information Protection and Electronic Documents Act (PIPEDA) Specifies how commercial business organizations can gather, retain, and share personal information
- Gramm–Leach–Bliley Act (GLBA) Specifies how financial institutions must protect and share the personal information of their customers
- General Data Protection Regulation (GDPR) Specifies data protection and privacy regulations for citizens of the European Union
These standards can define elements such as the following:
- The controls that organizations must exercise to protect the privacy of personal data
- How organizations can and cannot use personal data
- The rights of government and other official agencies to access personal data held by an organization
- The lengths of time an organization can and must retain individuals’ personal data
- The rights of individuals to access and correct their personal data held by organizations
Whether adopting certain standards is mandatory or voluntary, many organizations are concerned with whether the tools and procedures they use for storing and handling data comply with these standards.
Every organization must assess its own data resources and determine what standards should apply to them. The nature of the business in which the organization is engaged can often dictate compliance with particular standards. For example, companies in the health care industry or those with government contracts might be legally required to store, handle, and protect their data in specific ways. Indeed, there are regulatory standards to which Microsoft 365 products on their own cannot possibly comply, such as those requiring data to be stored on devices and in locations wholly owned and controlled by the organization, precluding cloud storage entirely.
However, many of the hundreds of privacy standards in use do allow the possibility of compliance when data is stored in the cloud, and Microsoft is well aware of the importance of adherence to these standards for many organizations considering a migration to the cloud. For IT professionals who are hesitant to become Microsoft 365 adopters because they fear that changing the location and the data storage conditions will negatively affect their compliance with standards like these, Microsoft has tested their products’ compliance with many different standards and published documents certifying the results.
Microsoft divides the compliance effort into three phases, as shown in Figure 4-11. The phases are described as follows:
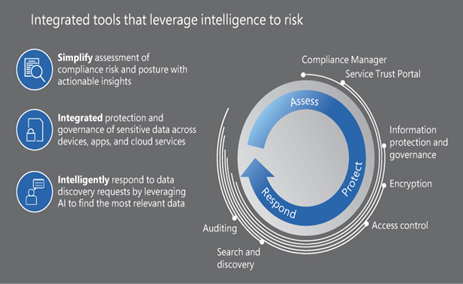
FIGURE 4-11 Microsoft compliance phases
- Assess The organization gathers the information needed to assess its current compliance status and produce a plan to achieve or maintain compliance with specific standards. Microsoft’s Service Trust Portal website contains a vast library of documents specifying information about the testing processes and the third parties involved in compliance testing. Also, Microsoft Purview includes Compliance Manager, a risk assessment tool organizations can use to record their actions to achieve compliance with specific standards.
- Protect The organization implements a protection plan for its data, based on its sensitivity, using the tools provided in the Microsoft 365 services, including access control permissions, file encryption, Information Protection, and Data Loss Prevention.
- Respond The organization develops protocols for responding to regulatory requests using artificial intelligence tools such as Microsoft 365 eDiscovery to perform complex searches of Exchange Online mailboxes, Microsoft 365 Groups, SharePoint and OneDrive sites, and Microsoft Teams conversations.
Need More Review? Microsoft 365 Compliance
For additional information on Microsoft 365’s compliance efforts, see the “Describe trust, privacy, risk, and compliance solutions in Microsoft 365” section in Chapter 3, “Describe security, compliance, privacy, and trust in Microsoft 365.”
Quick check
What is the difference between a Cloud Solution Provider that is an indirect reseller and one that is an indirect provider?
Quick check answer
- An indirect reseller is typically a smaller company concentrating on locating, cultivating, and signing customers for Microsoft cloud-based products and services. An indirect provider is a larger company engaged by indirect resellers responsible for supplying products, customer service, billing, and technical support services to customers.
