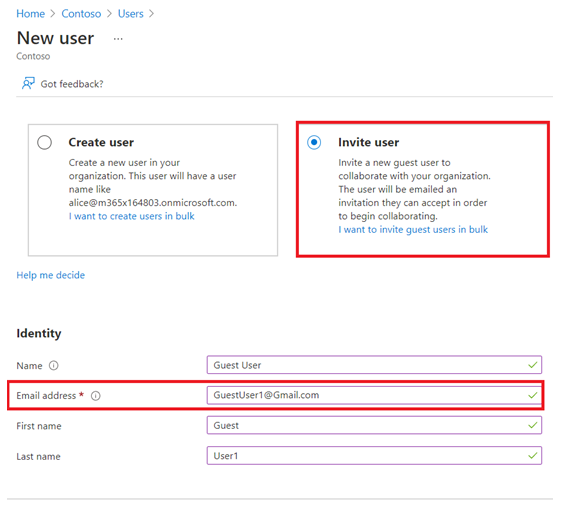
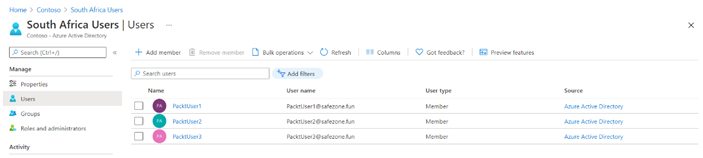
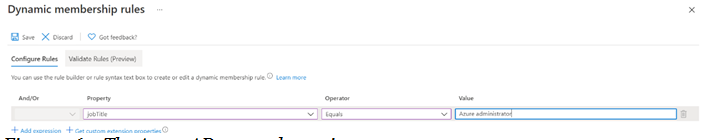
With Azure AD join, you are able to join devices directly to Azure AD without the need to join your on-premises Active Directory in a hybrid environment. While hybrid Azure AD join with an on-premises AD might still be preferred for some scenarios, Azure AD join simplifies the process of adding devices and modernizes device management for your organization. This can result in the reduction of device-related IT costs.
Your users are getting access to corporate assets through their devices. To protect these corporate assets, you want to control these devices. This allows your administrators to ensure that your users are accessing resources from devices that meet your standards for security and compliance.
Azure AD join is a good solution when you want to manage devices with a cloud device management solution, modernize your application infrastructure, simplify device provisioning for geographically distributed users, and when your company is adopting Microsoft 365 as the productivity suite for your users.
Azure AD join can be deployed by using any of the following methods:
- Bulk deployment: This method is used to join large numbers of new Windows devices to Azure AD and Microsoft Intune.
- Windows Autopilot: This is a collection of technologies used to preconfigure Windows 10 devices so that the devices are ready for productive use. Autopilot can also be used to reset, repurpose, and recover devices.
- Self-service experience: This is also referred to as a first-run experience, which is mainly used to join a new device to Azure AD.
When it comes to joining devices to Azure AD, there are two main ways of managing those devices:
- MDM only: This is when the device is managed exclusively by an MDM provider such as Intune.
- Comanagement: This is when the device is managed by an MDM provider and System Center Configuration Manager (SCCM).
When joining a Windows 10 device to Azure AD, there are two scenarios that we need to look at:
- Joining a new Windows 10 device via the Out-of-Box Experience (OOBE).
- Joining an already configured Windows 10 device to Azure AD.
Let’s take a look at how we can join an existing Windows 10 device to Azure AD:
- On the Windows 10 device, search for Settings and open Accounts.
- Select Access work or school, and choose Connect:
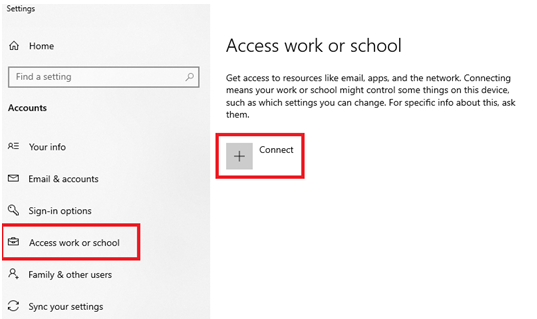
Figure 1.25 – The Windows 10 settings menu to add and connect a device to Azure AD
- Under Alternate actions, choose Join this device to Azure Active Directory:
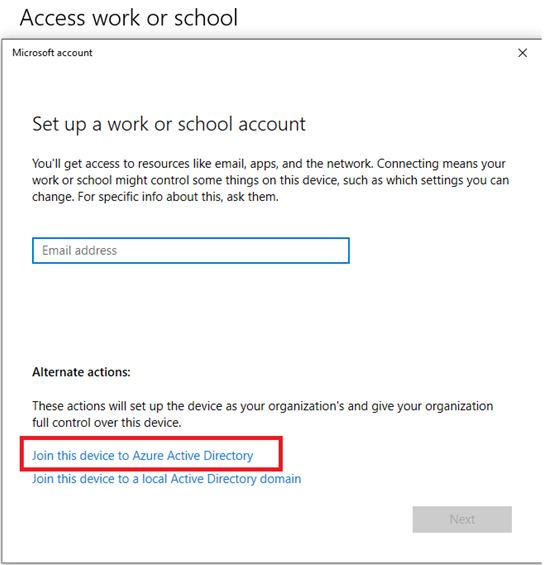
Figure 1.26 – TheWindows 10 device with the selected option to join the device to Azure AD
- A new window will pop up and ask you to sign in. Sign in with your organization’s account. In my case, this will be [email protected]:
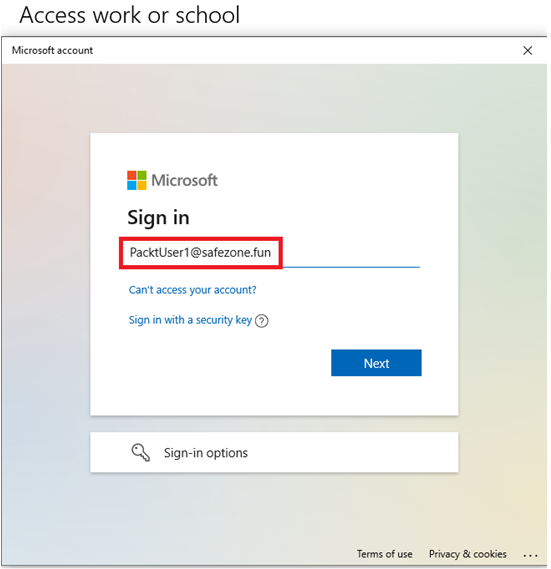
Figure 1.27 – TheWindows 10 device that requires you to sign in to an Azure AD account to join it to Azure AD
- You will be prompted to verify whether you want to join your domain. Proceed by clicking on the Join button:
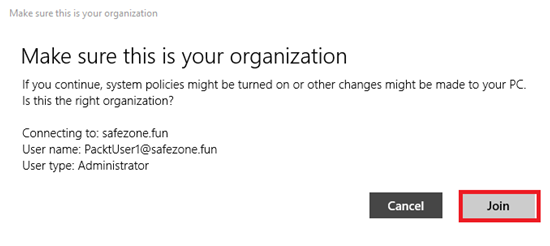
Figure 1.28 – The Windows 10 device summary page before joining it to Azure AD
- And now the Windows 10 device has been successfully joined to Azure AD:
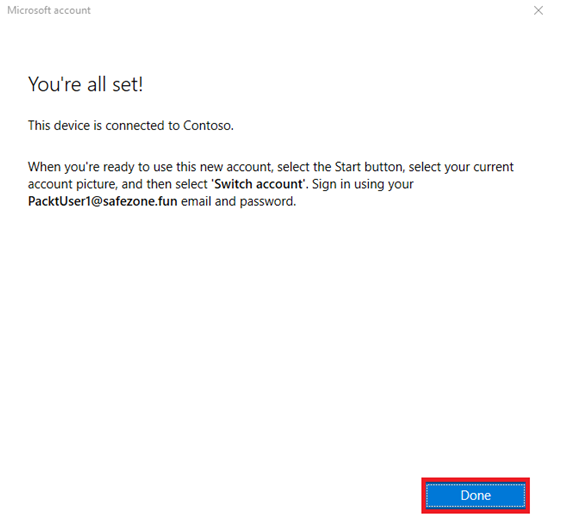
Figure 1.29 – TheWindows 10 device that has successfully been joined to Azure AD
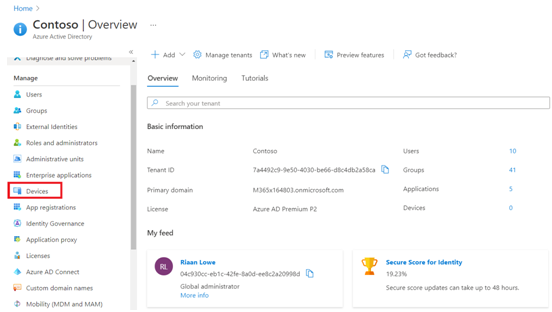
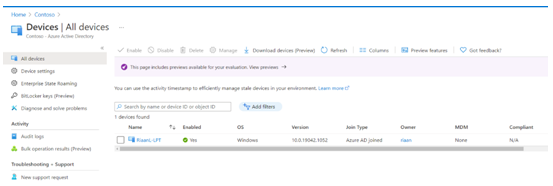
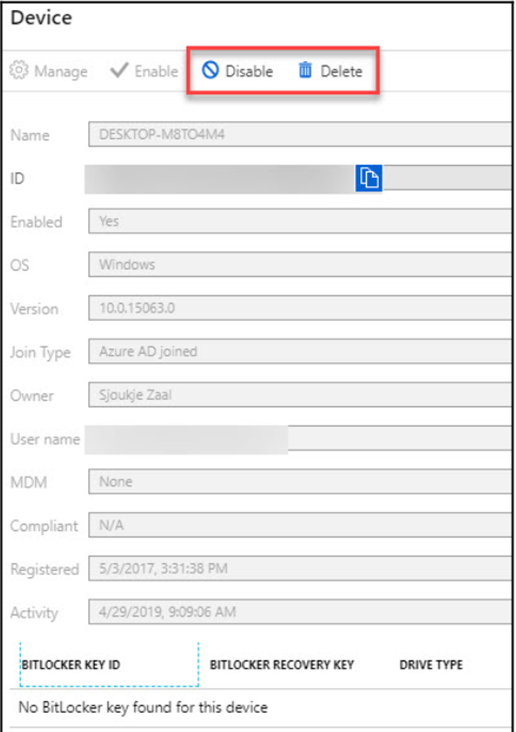
- As a final step, let’s navigate to the Azure portal under Manage, select Devices, and our newly Azure AD joined device will show up:
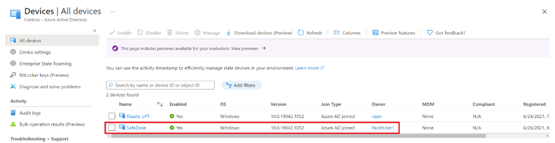
Figure 1.30 – Displaying the recently joined Windows 10 device in Azure AD under the Devices blade
That brings an end to this section. We have learned what Azure AD join is, the methods to enroll, and we have also shown the steps of how to manually join a Windows 10 device to Azure AD.
We encourage students to read up further by using the following links, which will provide additional information around Azure AD join, Windows Autopilot, and bulk device enrollment:
• https://docs.microsoft.com/en-us/azure/active-directory/devices/concept-azure-ad-join
• https://docs.microsoft.com/en-us/mem/autopilot/windows-autopilot
• https://docs.microsoft.com/en-us/mem/intune/enrollment/windows-bulk-enroll
• https://docs.microsoft.com/en-us/azure/active-directory/devices/azuread-joined-devices-frx
In the next section, we are going to take a look at SSPR.